Internet of Things (IOT)
The internet of things (IOT) refers to any device that connects directly to the internet and automatically sends or receives data.
In recent years there have been increased numbers of devices offered for use in business and at home that can increase the risk of a cyber-attack if proper precautions are not taken. The purpose of this document is to point out some simple safety precautions anyone can take to limit their exposure to cyber-attacks and/or cybercrime.
Examples of some IOT devices readily available to and already widely used by consumers:
- Automated thermostats
- Garage door openers
- Cloud data storage devices
- Video doorbells
- Remote spa/pool control devices
- Smart appliances such as televisions and refrigerators
- Baby monitors
- Security systems and cameras
What are the risks?
IOT devices require a connection to the internet in order to update their software and otherwise perform the functions for which you bought them. This connection is done through your home router which is usually the device provided by your internet service provider or cable company. The IOT devices communicate to other devices on your network (devices also attached to your router) and through the internet on their own using preset user names, passwords, and protocols making the device simple to set up and get working. Cybercriminals rely on the fact that most people do not change the default user names and passwords to gain access to your device. It only takes one such device on your network to corrupt the entire network.
What can you look for to determine if your system has been compromised?
- Increase in network traffic resulting in slow connectivity to devices and the internet
- Devices listed under the network directory that you do not recognize
- Devices that are sending/receiving data more than they should
Slow internet connection will be the most obvious clue which is sometimes indicated by a website loading slowly or your Smart TV not buffering video fast enough. Although this could be attributed to other conditions it is worth checking out if you notice it.
Most people know how to find files on their computer by using a file explorer to select drives on their computer. Using that same program, you can select “Network” and it will list all devices connected to your network. Review the list periodically for devices you do not recognize and remove them.
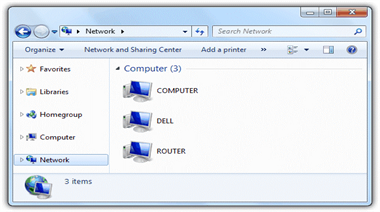
Most of these devices, once set up, should not be sending/receiving data for anything but short periods of time when you are accessing them or when they are updating themselves. If you notice a device is constantly sending/receiving data then it is possible it has been compromised. Some devices have a light on them which illuminates when data is being transferred, but other devices do not indicate data transfer visibly. There are network monitoring software programs available that can be configured to alert you when suspect network traffic is detected. There are free, trial and paid versions available depending on your needs, but most home and small business networks can be sufficiently monitored with the free software (paid versions just allow a larger number of devices or data points to be monitored).
What can you do to protect your network?
- Create your own user names and passwords and disable the defaults on all devices to include your router.
- Turn on the firewall on your computer and your router
- Turn off universal plug and play protocols
- Update the software and firmware on your computer, router, and devices regularly
- Limit the visibility of your Wi-Fi devices.
Creating your own user names and passwords is the easiest way to limit your risk of cyber-attack. The act of creating a user name and password most often will disable the defaults set on the devices, but read the instructions for your device and ensure the defaults are in fact gone or disabled. Also, use strong passwords that contain a combination of letters, numbers and characters. Avoid using simple words or phrases and consider using different user names and passwords for different devices.
Most computer operating systems in use today provide a firewall program that you can configure to secure your network. Routers also come with a firewall to use similarly. Parents can also use the firewall to limit the time and manner their child’s devices connect to the internet through the network!
Universal plug and play protocols allow consumers to quickly and easily set up their device and begin using it. These same protocols also make it easy for cybercriminals to connect to your device. Disable these protocols after you have set up your device. You will have to refer to your device user manual as the procedure varies by device.
Your devices usually have two programs that allow it to work, firmware and software. Most people are familiar with software as it is what allows you to interact with your device. The firmware is software your device has built into it that operates behind the scenes and allows it to function. It is most noticeable when you first turn on your device and it begins to “wake up.” It is important to update these programs so they have the most up to date security features. Most software has the ability to conduct automatic updates, which simplify security processes for users. Firmware most often requires you to do something to update it. It will usually prompt you to update the firmware in which case just follow the instructions, but some devices require you to manually check for updates. The user manual for your device will have information on this.
Devices come with the Wi-Fi name (SSID) of the device visible to anyone. It makes it easy to setup your devices and (you can see a common theme here) it also makes it easy for cybercriminals to access your device. Making a device invisible will require you to manually enter the device name when setting up instead of automatically detecting, but it is only one additional simple step in exchange for increased security. The router is the main piece of equipment you should make invisible and other devices may require you to use a setting that makes them visible only to synchronized devices or those already on the network. You will have to read your user manual to determine the procedure and best setting for each device.
Lastly, you should know that following these rules will make your devices and computer network less vulnerable to attack, but will not make them impervious. You need to remain vigilant and quickly remove a device from your network that has been compromised until it can be fixed. If you cannot remove it from the network then cut off the devices connection to the internet.
Law enforcement should be contacted if someone accessed your device, computer, or computer network without your authorization and you can articulate a loss.
You can find additional information on this and other topics at the following websites:
National White Collar Crime Center
Internet Crime Complain Center